Decentralize decision-making without the risk
Request a demo
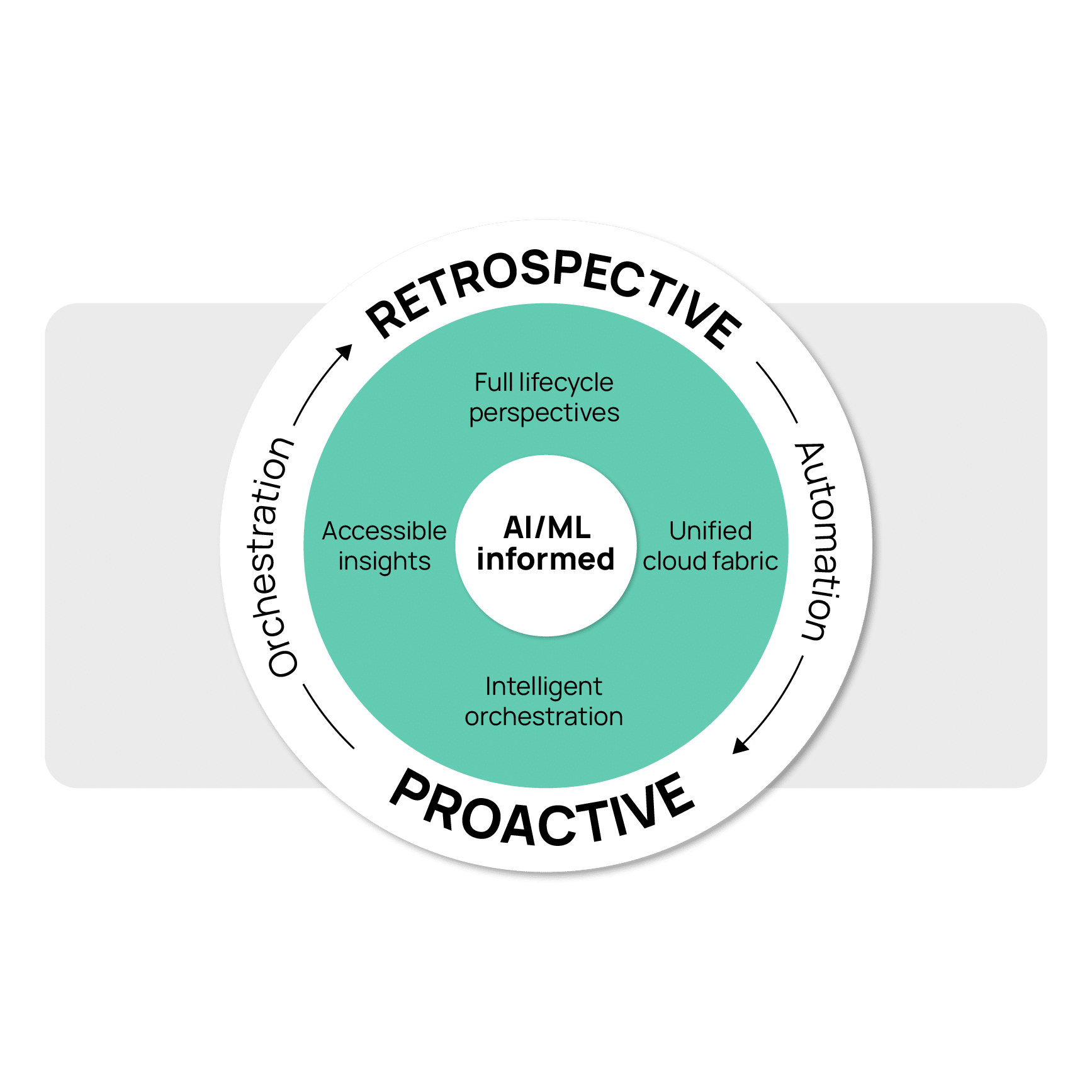
Confidently accelerate cloud adoption
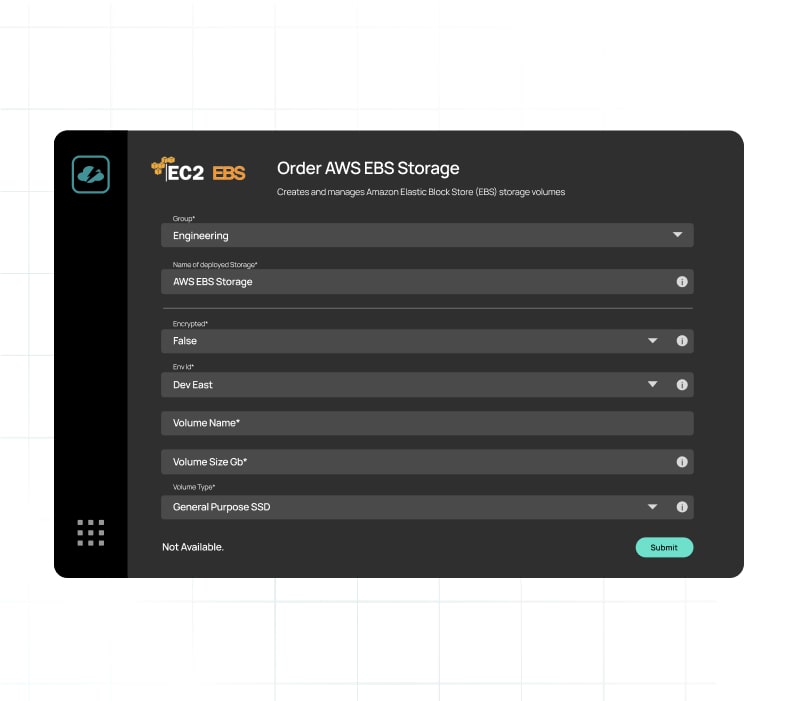
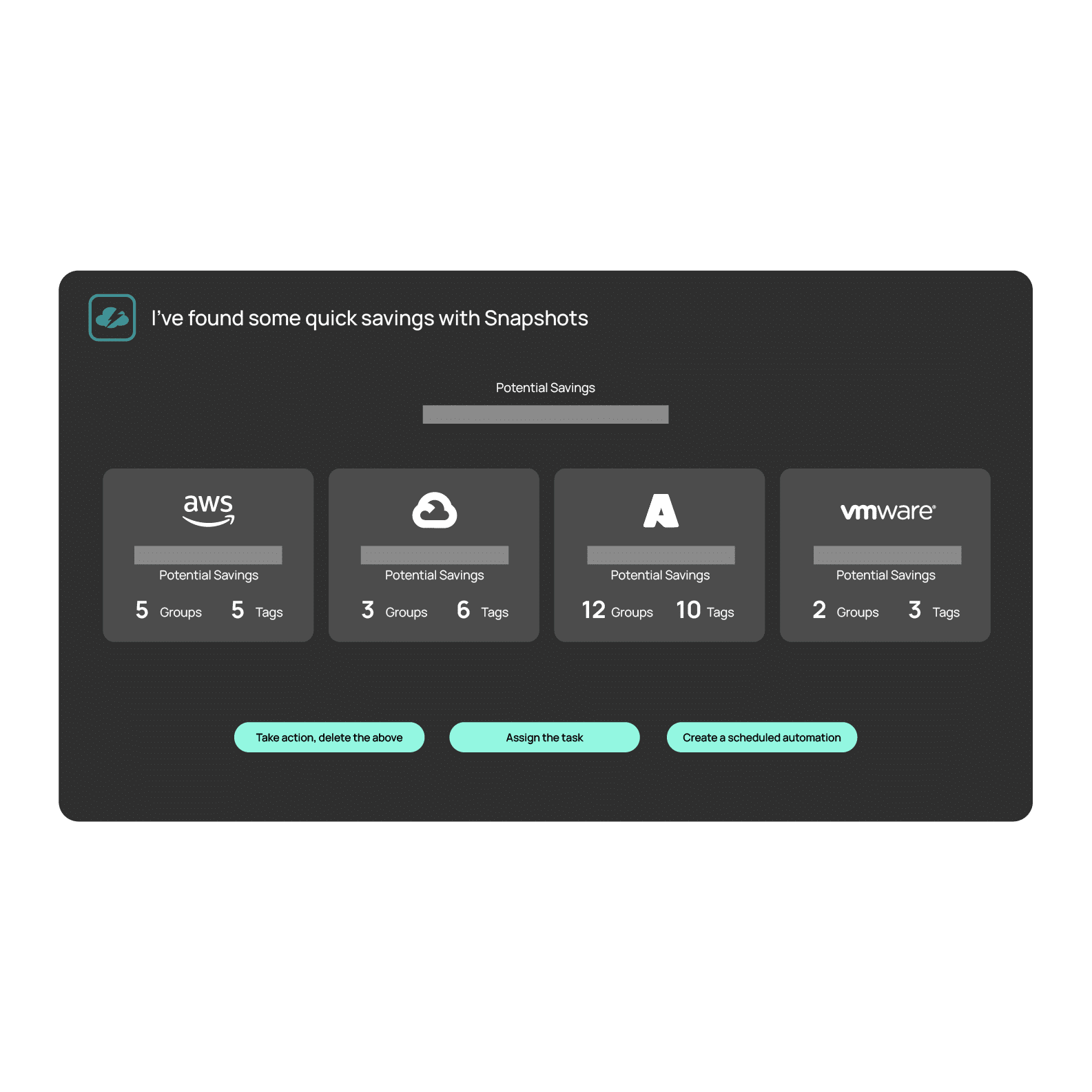
Elevate efficiency, reducing decision-making time
CloudBolt’s approach to policy enforcement in the DevOps lifecycle accelerates release velocity without compromising oversight. By shifting policy enforcement, testing, and approvals earlier, it enables faster, more efficient decision-making. Regulations are embedded as code with automatic validation, fostering an environment of innovation with reduced risk.
At its core, CloudBolt ensures technical leaders retain visibility and control, empowering teams within secure, policy-driven guardrails. Automated compliance checks, restricted self-service consumption, and layered security integrations build oversight by design. This holistic approach to cloud management not only saves time but also empowers organizations to operate more effectively in the cloud.
Put a financial focus in cloud development
Promote responsible financial decisions among developers using preemptive steering. CloudBolt gives development teams the tools they need to model deployment costs, automate tagging, create t-shirt sizing and much more, simplifying decision making and promoting a culture of fiscal responsibility.
Uncompromised security and compliance
Elevate the security and compliance of your cloud. CloudBolt integrates your specific requirements – from security protocols to compliance mandates and network configurations – directly into each new build, ensuring they meet the highest standards of protection and compliance right from the start.

Clarity, security, and seamless integration

Contextual access and permissions
Enforce least privileged access and zero trust security models using role-based access control, single sign-on, or OAuth protocols, enhancing security and trust.

Approval frameworks
Implement triggers for approval processes tailored to public and private clouds, using your preferred ITSM or chat tools, ensuring efficient and controlled cloud actions.

Alerting and communication framework
Incorporate alerting and chat integration with tools like Slack, Teams, Email, and custom integrations like PagerDuty, facilitating timely notifications and efficient communication for different groups and services.
Full-lifecycle financial governance

Budget-aware deployments
Define budgets at the group or resource level, integrating with existing financial data sources, and set custom alerts.

Cost modeling
Leverage real-time modeling of cost estimates pre-deployment, enabling data-driven provisioning aligned to capacity.

Cost quotas
Define quotas that specify either the maximum number of resources or the maximum cost teams can allocate.

Automated resource scaling
Autoscaling seamlessly responds to changes in demand, scaling infrastructure up or down based on predefined metrics.

Lifecycle administration
Proactively identify unused resources and decommission based on policies or integrate with DevOps toolchains.
Built-in safeguards for worry-free innovation

Secure DevOps acceleration
Shift security left in the software lifecycle by codifying and version controlling guardrails as code through CloudBolt. Reduce remediation costs via earlier integration testing for policy compliance.

Continuous infrastructure testing
Enable better CI/CD by proactively validating infrastructure provisioning and configurations through data protection, pipeline health validation, network isolation, and downstream tool integration tests.

Extensive security integrations
Achieve layered risk protection through 150+ joint integrations with leading tools like Palo Alto, Hashicorp, Splunk and CyberArk.
Don’t just take our word for it
You can do entire lifecycle management using the CloudBolt framework.
Developers are overwhelmed by the amount of security configurations that are needed to secure the cloud… with CloudBolt, they will no longer have to be security experts or worry about creating vulnerabilities for the organization.
See CloudBolt in action
Request a demo

More resources

The Truth About Cloud Value
Are you navigating the complexities of cloud transformation and seeking effective strategies to optimize your investments? This white paper is an essential resource for understanding the financial realities of cloud transformation strategy. It’s designed to guide enterprises through the intricacies of cloud computing, debunking common myths and setting the stage for successful cloud adoption. In […]
Augmented FinOps: The Next Era for Cloud Cost Management
Augmented FinOps is an innovative approach that integrates artificial intelligence with financial operations, aiming at optimizing cloud cost management. This resource is specifically crafted for IT leaders, financial experts, and those keen on understanding and implementing pioneering strategies in cloud computing. In This White Paper, You Will Discover: Key Topics Explored: Transform Your Cloud Financial […]